Reverse Engineering writeup | IDSECCONF 2020
12 December 2020, My team TNT has participated in the IDSECCONF CTF Competition, we ranked 11th since we have to prepare for 13 December 2020 (redmask CTF final). so we don’t have so much time to play there. on this CTF I solve some Reverse engineering challenge, in this post I will cover some rev challenge that I solve during the competition.
Pemanasan
firstly unpack the binary using upx then jump to the cetak function
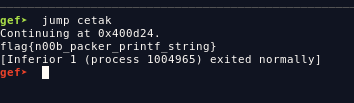
FLAG: flag{n00b_packer_printf_string}
Peregangan
another simple challenge, let’s set a breakpoint on
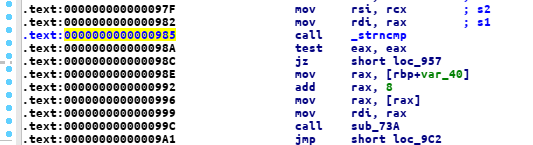
then run the binary on gdb, as you can see, our input AAAAAAAA is compared to a string ttynyxluuu
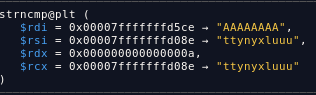
so the password is ttynyxluuu. now in order to print out the flag, we have to patch this binary from je 0x957 to jne 0x957
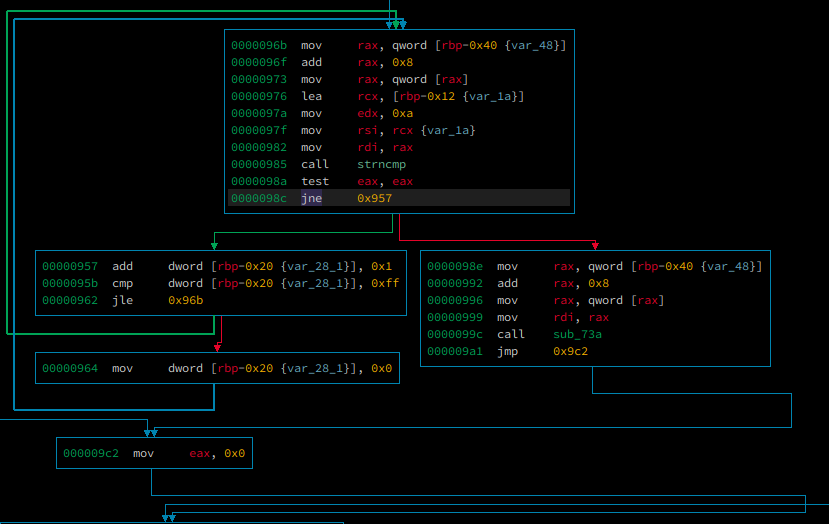
now just run the binary
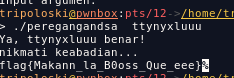
FLAG: flag{Makann_la_B0oss_Que_eee}
Pernafasan
this is the main function
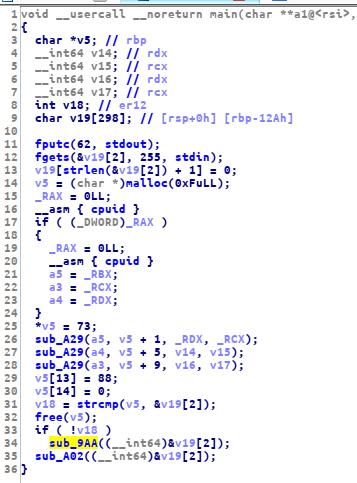
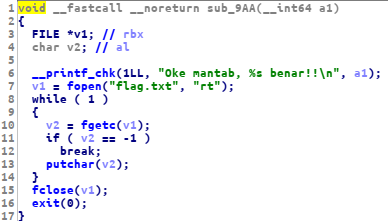
the flag is on the sub_9AA function
after debbugging, i found that our input is compared to IAuthenticAMDX
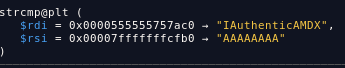
this string comes from my cpu vendor_id since I use AMD machine my vendor is AuthenticAMD and the program is concated I and X. the server
is using intel cpu, so the vendor_id is GenuineIntel so we can just append the string I and X, this is my full exploit
#!/usr/bin/env python2
'''
author : tripoloski
visit : https://tripoloski1337.github.io/
mail : arsalan.dp@gmail.com
'''
import sys
from pwn import *
context.update(arch="amd64", endian="little", os="linux", log_level="debug",
terminal=["tmux", "split-window", "-v", "-p 85"],)
LOCAL, REMOTE = False, False
TARGET=os.path.realpath("/home/tripoloski/code/ctf/idsecconf2020/pernafasan/pernafasan")
elf = ELF(TARGET)
def attach(r):
if LOCAL:
bkps = []
gdb.attach(r, '\n'.join(["break %s"%(x,) for x in bkps]))
return
def exploit(r):
# attach(r)
p = "IGenuineIntelX"
r.sendline(p)
r.interactive()
return
if __name__ == "__main__":
if len(sys.argv)==2 and sys.argv[1]=="remote":
REMOTE = True
r = remote("139.180.185.160", 4000)
else:
LOCAL = True
r = process([TARGET,])
exploit(r)
sys.exit(0)FLAG: flag{ges3rin_sc0remu_0m}
 Hello I am Arsalan. Offensive Security Engineer, I blog about Cyber security, CTF writeup, Programming, Blockchain and more about tech. born and raised in indonesia, currently living in indonesia
Hello I am Arsalan. Offensive Security Engineer, I blog about Cyber security, CTF writeup, Programming, Blockchain and more about tech. born and raised in indonesia, currently living in indonesia